Encryption Basics | Really Private Messaging
Made by Mozilla with thanks to April King's "Intro to Cryptography", released under the CC-BY-SA license
45 minutes
Participants will learn the basic importance and mechanics of encryption, modeling public-private key encryption schemes with simple tools like paper and markers, crayons, or colored pencils, thereby learning how to collaborate, connect, evaluate encryption schemes, and secure their communications online..
Web Literacy Skills
21st Century Skills
Learning Objectives
- Understand encryption as a way to keep private information secret from eavesdroppers.
- Understand how public-private key encryption works (a.k.a. asymmetric or RSA encryption).
- Create simplified public and private keys to model asymmetric encryption.
- Understand encryption best practices for beginner users.
Audience
- 13+
- Beginner users of encryption.
Materials
- Internet-connected instructor computer
- Markers, colored pencils, crayons, paints, or any other coloring tools that easily mix.
- Paper
- Internet-connected computers for participants
-
1. Introduction
10 minutesWith thanks to April King!
We all value our privacy online - especially when we're sending messages to a friend or family member that we don't want anyone else to read! Encryption - the practice of making our private messages encoded and more secure from prying eyes - is one tool that makes things like private messaging possible.
Encryption has been around for thousands of years.
Originally, encryption helped allied military leaders communicate their plans with one another while keeping their enemies in the dark. Some of the earliest ciphers, or codes, were Caesar Ciphers. These ciphers swapped letters to scramble messages by shifting each letter to a different letter a certain number of spaces away in the alphabet. The sender and recipient knew how to unscramble the letters, but since some letters show up more frequently than others, eventually the frequency of the encoded letters let enemies break one another's codes.
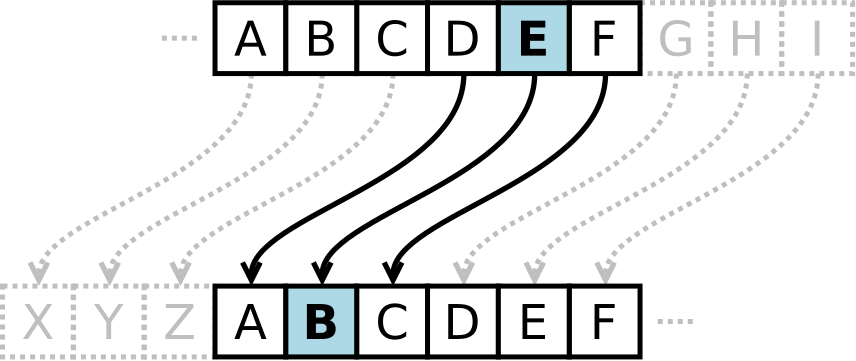 "Caesar cipher left shift of 3," CC0 Public Domain by Matt_Crypto
"Caesar cipher left shift of 3," CC0 Public Domain by Matt_Crypto
Try your own Caesar Cipher using this pen from MattC.K:
Type your message into the textbox, pick a number of letters to shift, and your newly encrypted message will appear.
Take a moment to do the following:
- Write a short message to someone else at the workshop or to a friend.
- Encrypt the message using the form above.
- Send your workshop partner or friend the message along with your cipher - like "Caesar Cipher shift 5" - so they can decode it.
- Decode any messages people send you.
- Think about how easy or difficult it would have been to decrypt the messages you sent and received if you didn't have the key. Would it have been easy? Impossible? Would it just have taken some time? How much, would you estimate?
Today, after solving problems once thought impossible, cryptographers have created sophisticated, two-key encryption systems that allow for privacy and trust between sender and recipient. We'll explore one of those methods next called public-private key encryption.
-
2. Encrypting with Public and Private Keys
10 minutesIn the mid seventies two teams of cryptographers published "public-key" encryption systems. In 1976, Whitfield Diffie and Martin Hellman published what is now known as the Diffie-Hellman key exchange protocol, and in 1977, Ron Rivest, Adi Shamir, and Leonard Adleman shared public-key encryption with the world. This system is sometimes called "RSA encryption" after the initials of its inventors.
These techniques power a lot of the encryption you already use today, so it is useful to know how they work. These systems use complex algorithms to generate complex keys that work in pairs to independently encrypt and decrypt messages between two parties. The keys also validate each party's identity to the other to help prevent man-in-the-middle attacks.
Here's an example of a Diffie-Hellman encryption system that uses color to explain how it works. Watch from the beginning through 2:10 to get an idea of how these color keys work.
Simply put, public-private key encryption lets you create a pair of keys that talk to one another like so:
- You create a public key that anyone can see. People use this key to encrypt messages they send you. Once someone encrypts a message with this key, that same key cannot decrypt the message at all - the math is all wrong for that.
- At the same time you create your public key, you create a private key that you must keep safe from everyone else. It goes with your public key. Whatever your public key encodes, your private key can decode.
- When you receive a message encrypted with your public key, you can decode it with your private key.
- You can also "sign" a message with your public key (by attaching it to a message encoded with the recipient's public key) so that its recipient can trust that you sent the message.
In this scheme, even if a "man-in-the-middle" eavesdropper manages to intercept, read, or steal your message, that person will be missing the second key needed to decrypt it.
These systems matter so much because without such strong encryption, anyone can easily read the private communications intercepted online. However, if we use strong encryption, even if someone intercepts our private communications, it’s highly unlikely they will be able to read what we've sent. If we agree to let a government break or outlaw our encryption schemes, it hasccess to all of our communication with one another, as will bad actors.
Next, we'll get together with a partner and try encrypting colors of our own to see first-hand how this kind of public-key encryption works.
-
3. A Note on Crypto
5 minutesWhile we're going to play around with color to learn how public-private key encryption works, it's important to know that we're "playing" with encryption today to see how it works. Don't write your own "crypto" after today's activity. The kinds of systems we can come up with on our own are weak and easily breakable by others and by computers. If you need help encrypting your communications, you should use standard tools available to everyone. Check out this page from the Freedom of the Press Foundation for helpful hints. When we set up encryption correctly on our computers, our computers do most of the work.
Not even the experts get everything right, but it's better to use the experts' crypto than our own.
-
4. Creating Color Keys
15 minutesLet's try to create some Diffie-Hellman color keys ourselves! You can revisit the video from Step 2 - Encrypting with Public and Private Keys to see how this works and illustrate the instructions below.
- First, even before you get a partner, grab a marker, crayon, or other coloring tool from the workshop supplies and try to keep it totally secret. Your facilitator may call you up one by one to grab a color, or she may pass out colors sealed in envelopes to help with this step.
-
Once your secret color is secure, Find a partner at the workshop (or grab a friend). Make sure you understand the basics from the video in Step 2 - Encypting with Public and Private Keys. Ask any questions you still have before we begin. Here is an illustration of the system we're trying to create:
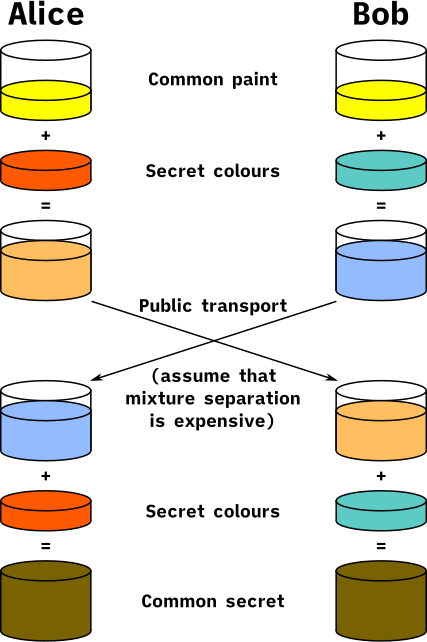
Illustration of the Diffie–Hellman Key Exchange, CC0 Public Domain by A.J. Han Vinck - At this point you and your partner should each have a secret color. These are your private keys.
- If that's the case, grab a third color. This is your public key. You, your partner, and everybody else can see it.
- Grab two pieces of paper - one for you and one for your partner.
- Color a large portion of each paper with your third, public key color.
- Move away from your partner and color over that public key color with your private key color. Color thoroughly, but stay inside the original patch of color so that you don't give your private color away by coloring over blank parts of the page.
- Meet your partner again.
- Exchange papers. You should have a paper that has your public key color mixed with your partner's private key color.
- Move away from your partner once more.
- Add your color to the mix of the public key color and your partner's private key color. Again, color thoroughly, but stay inside the original patch of color.
- Team up with your partner one more time.
- Compare your "messages" - or pieces of paper. You should both have a similar color made up of your public key color and both partners' private key colors.
- Spend the rest of the time left for this step visiting other groups. Can anyone guess either of your private key colors from your group's mixture? Can you easily guess other people's private key colors?
Imagine huge, interrelated public-private numbers and their factors interacting in a similar way and you've grasped basic cryptography and encryption. My number, your number, and a shared number talk to one another in a unique relationship that would take even a computer years and years and years to crack.
-
5. Reflection
5 minutesTake a few moments at the end of the lesson to gather together again as a whole group. Join in a facilitated conversation about encryption basics answering questions like these - or ask your own questions of the group!
- In general terms and in your own words, can you summarize how public-private key encryption works?
- How does encryption connect to privacy and security?
- What are some situations in your own life in which you want your private information to stay private between you and another person?
Congratulations on working through the basics of encryption - while it's tough to learn and even tougher to write, it's important to understand how encryption protects your privacy and communications online. How else can we all teach about the importance and mechanics of encryption? Whom else can you teach in your community or at home?